TOTPRadius Two-factor authentication for Citrix Storefront with self-enrolment
Configuring Citrix Netscaler Gateway to use TOTPRadius
In order to enable two-factor authentication on Netscaler gateway, we have to specify TOTPRadius as secondary authentication for XenApp/XenDesktop site.
Login to Netscaler admin panel with nsroot and click on Configuration->XenApp and Xendesktop sites->Configured Virtual Servers . Click on Edit button next to the site you want to configure two-factor authentication for.
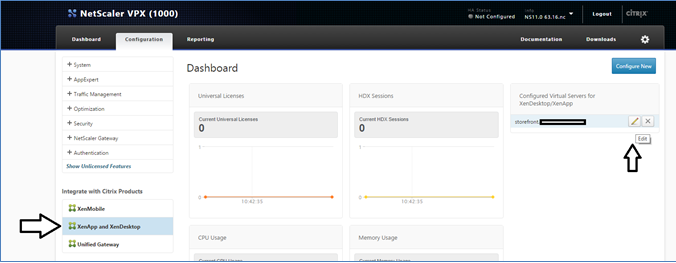
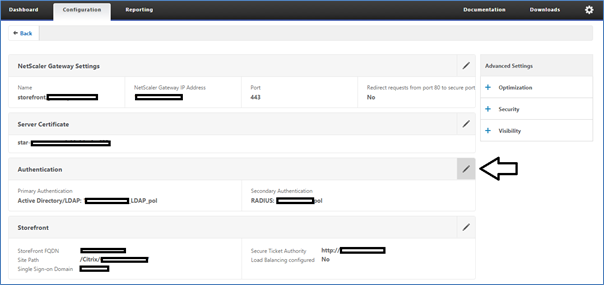
Click on edit icon on the Authentication box.
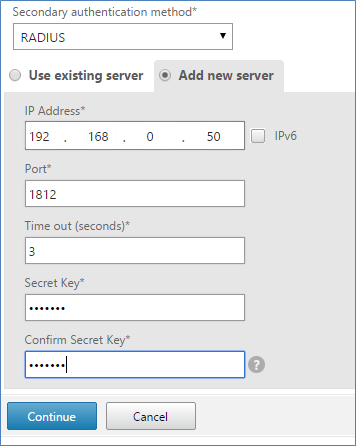
Set "Secondary Authentication Method" to RADIUS and enter the TOTPRadius appliance settings in the form below. Leave port as 1812. Radius secret is as specified in Admin Panel of TOTPRadius web interface.
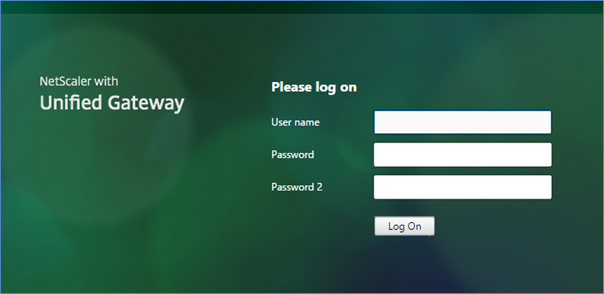
Click on "Continue", then "Done". Once done, Netscaler interface will ask for two passwords (Password 2 is the field for OTP).
Enabling user self-enrolment via Citrix StoreFront interface
TOTPRadius provides a RESTful API service to allow StoreFront integration. You have to install StoreFront integration package (described below) on all StoreFront servers in the cluster. Once installed and configured, users will see an additional status bar in the header prompting users to enable TOTP.
Note! You should set "Allow initial login" to at least "1" in TOTPRadius Admin Panel to allow users to login and enrol second factor authentication.
Enrolment process
Storefront will use API calls to check if the current user has a TOTP profile enabled on the TOTPRadius server.
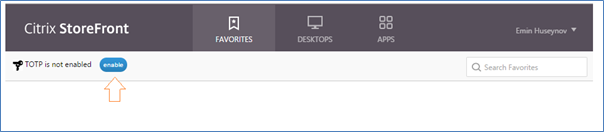
To enable TOTP, users should click on "enable", then on OK button on the next popup.
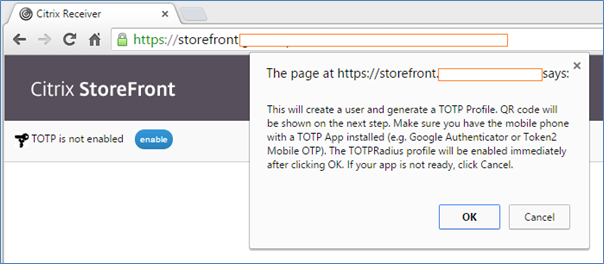
After
clicking OK, StoreFront will send an API call to TOTPRadius and enable
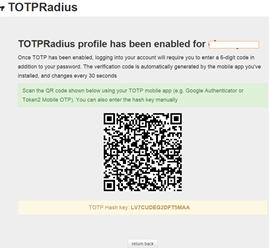
second-factor authentication for the user immediately. QR code will be shown,
and user should scan it with a TOTP mobile application (Google Authenticator,
Token2 Mobile OTP etc.)
On the next login, the user should provide OTP generated by the mobile app in
order to login.
Users that enrolled themselves will still appear on TOTPRadius web interface
and can be edited, banned or deleted by administrators.
Installing integration package
Download the TOTPRadius Storefront integration package and run the installer as administrator on the StoreFront server.
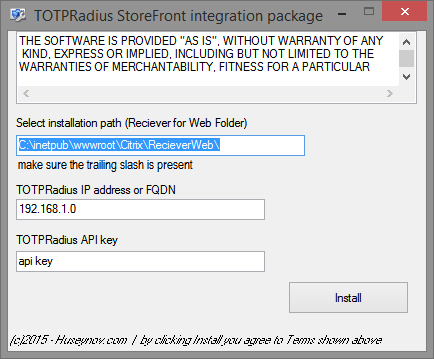
-
Specify the folder where your Reciever for Web Website is located. Make sure
you include a trailing slash at the end.
- Enter the IP address of the TOTPRadius appliance. You can use FQDN if DNS is
properly configured on all 3 components (Netscaler, TOTPRadius and StoreFront)
- API key (you can view/change it in TOTPRadius admin panel)
Note! Netscaler pass-through configuration should be done correctly in order for this customization to work. You can test it by accessing <YOUR_WEB_URL>/DomainPassthroughAuth/test.aspx . The page should show current user's domain, username and authentication type.
Note! Netscaler RADIUS authentication policies should be configured to send username only (otherwise 2FA may be bypassed using DOMAIN\username or username@domain UPN)
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
21-12-2025
Android, NFC, and the Missing Piece of WebAuthn
 For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
09-12-2025
Framework ExpansionCard Enclosure for Token2 Keys
 Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
