TOTPRadius - Single factor authentication configuration options
TOTPRadius can be used as an LDAP Proxy, or to be more correct, RADIUS to LDAP Proxy. In this configuration, the user authentication is done against 2 sources: the password is verified by the upstream LDAP server(s), and the OTP is checked by the TOTPRadius itself locally. In some use cases, there is a need to exceptionally allow using a single factor authentication against TOTPRadius. This may be needed to provide access to system or other generic accounts used, for instance, in automated scripts, where the second factor is not possible to be entered.To address this issue, you can use one of the following options.
User level setting
You can set this behavior at the user level, but changing the 'Allow single factor' value to 'Enabled'
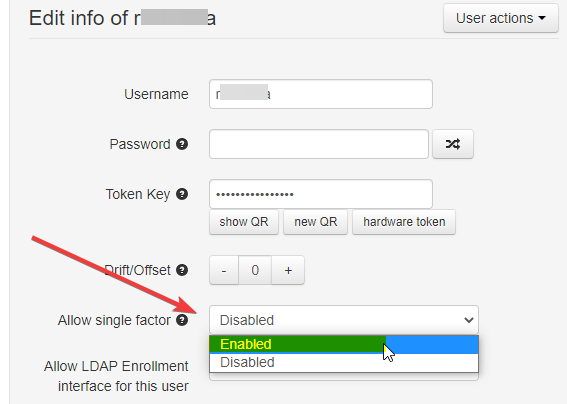
This will allow this particular user to log in using LDAP Password + OTP, OTP only, or LDAP Password only.
Please note that the LDAP Password only option will work for TOTPRadius v 0.2.7 or newer.
Subnet level
Starting from TOTPRadius v0.2.9, it is also possible to allow single factor logins from a trusted IP range. This setting is called 'Trusted IP Configuration' and can be set in the Settings → Advanced Settings section.
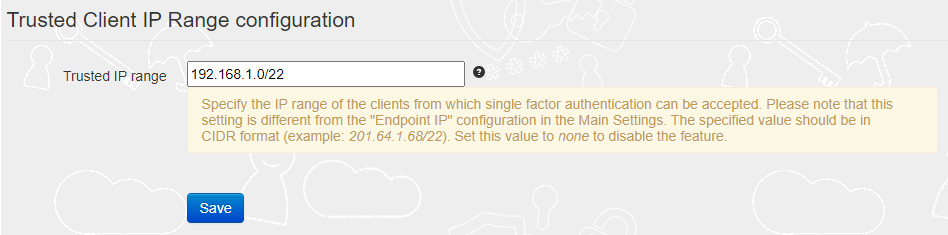
The value is expected in CIDR format. To disable this functionality, set the value of this field to 'none'.
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
21-12-2025
Android, NFC, and the Missing Piece of WebAuthn
 For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
09-12-2025
Framework ExpansionCard Enclosure for Token2 Keys
 Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
