Default MFA Method for Microsoft Entra ID Users
Users often ask how to change the default authentication method for a user in Microsoft Entra ID. This method is referred to as the 'user-preferred multi-factor authentication method'. However, the authentication process sometimes does not honor the method set as the default. Why does this happen? It's because the 'user-preferred MFA method' has a lower priority than the 'system-preferred multi-factor authentication method'.'System-preferred multi-factor authentication (MFA)' is a feature in Microsoft Entra ID (formerly Azure AD (Microsoft Entra ID)) that allows the system to determine the most secure authentication method available to the user at the time of sign-in.
As of the time of writing, the system-preferred method is FIDO2, and it is unlikely this will change in the near future—unless a method even more secure than FIDO2 is developed.
Manage Default MFA Method for Users in Microsoft Entra ID
Previously, admins couldn't change the default sign-in method through the UI. However, Microsoft has introduced a preview feature that allows Entra ID admins to set the default MFA method using Microsoft Entra ID. This setting is ideal for admins who want to help users transition from less secure MFA methods to stronger ones as the default. Admins can follow the steps below to update the default MFA method for each user individually. Also, admins should disable system-preferred MFA in the tenant before delving into the steps below.1. Navigate to Microsoft Entra admin center → Users → All Users.
2. Choose the specific user whose default MFA method needs to be modified.
3. Under the respective user’s page, click ‘Authentication methods’ from the left tab.
4. Now, click the edit icon near the ‘Default sign in method’ option.
5. Then, choose the preferred MFA method from the drop-down box and save the changes.
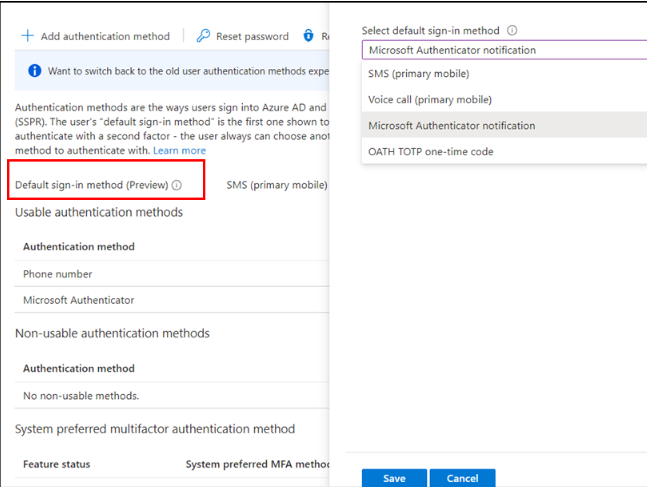
Once configured, the specified method will automatically become the default multi-factor authentication method for that user and will be prompted during the sign-in process.
Configure Default MFA Method Using Microsoft Graph API
Admins can make use of Microsoft Graph Explorer to update the default MFA method for a single user. To do so, admins need to use the Graph API below.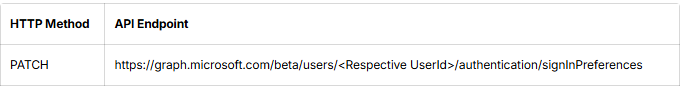
with body:
{
"userPreferredMethodForSecondaryAuthentication": "MFAMethod"
}
The different MFA methods you can set are:push – push notification in Microsoft Authenticator.
oath – 6 digit code from authentication app.
voiceMobile – Microsoft call upp your primary mobile phone.
voiceAlternateMobile – Microsoft call upp your alternate mobile phone.
voiceOffice – Microsoft call upp your office phone.
sms – 6 digit code from SMS text message to the mobile phone.
Admins should specify the respective user ID in the API and grant consent for “UserAuthenticationMethod.ReadWrite.All” and “UserAuthenticationMethod.ReadWrite” permissions in MS Graph Explorer. After completing the permission setting, admins can run the API with the JSON format given above.
Configure Default MFA Method via My Security Info
By default, users can choose their preferred MFA method at https://mysignins.microsoft.com/security-info.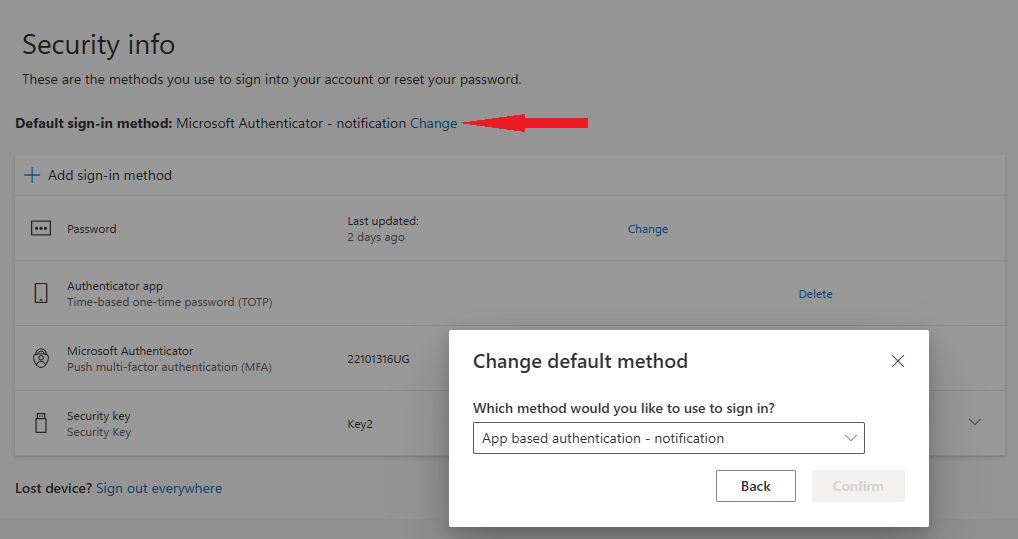
Note: The list of available methods depends on which methods the user has enrolled. At least two methods must be enrolled for the option to set a default method to appear.
Retrieve system-preferred MFA method information
Now let’s take a look at what the data looks like when a user is enabled for the system-preferred authentication method:1) In the Microsoft Entra admin center, go to the respective user's page and click on 'Authentication methods' in the left-hand menu.
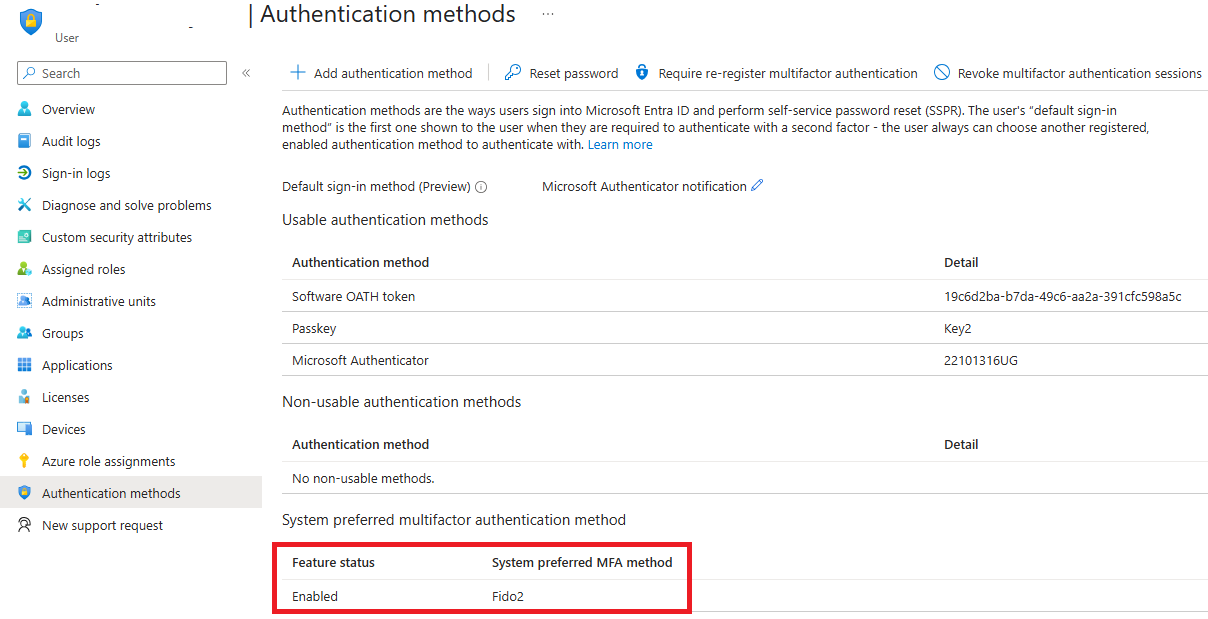
2) Get information using the Graph API directly
GET https://graph.microsoft.com/beta/users/{userID}/authentication/signInPreferences
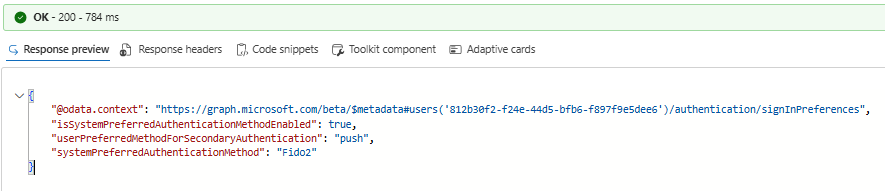
The response will have three values:
isSystemPreferredAuthenticationMethodEnabled-Indicates whether system-preferred method is enabled for this user
userPreferredMethodForSecondaryAuthentication-The default second-factor method used by the user when signing in
systemPreferredAuthenticationMethod-If system-preferred method is enabled, it will show the default/strongest method
Manage system-preferred MFA in the Microsoft Entra admin center
By default, system-preferred MFA is Microsoft managed and enabled for all users.1) Sign in to the Microsoft Entra admin center as at least an 'Authentication Policy Administrator'.
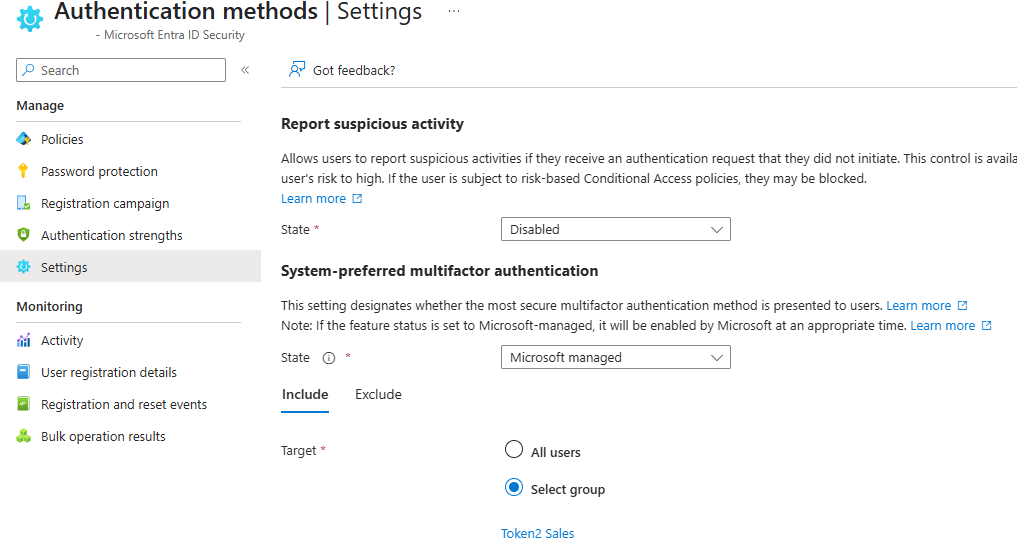
2) Browse to 'Entra ID > Protection > Authentication methods > Settings'.
3) For 'System-preferred multifactor authentication', choose whether to explicitly enable or disable the feature, and include or exclude any users. Excluded groups take precedence over include groups.
For example, the following screenshot shows how to make system-preferred MFA explicitly enabled for only the 'Token2 Sales' group.
Classic tokens with Entra ID
Entra Passwordless
- Automated Registration for Entra ID with PowerShell and GraphAPI
- Enrollment guide (standard)
- Enrollment guide (using Temporary Access Pass)
- Configure workstation passwordless login (Intune method)
- Configure workstation passwordless login (registry modification method)
- Configuring iPhone Mail apps for users only with Passwordless access
- Default MFA Method for Microsoft Entra ID
Other Entra ID/MS365 Guides
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
