Using the same hardware token for UserLock and Office 365
 UserLock is a user login security system for on-premises Windows Active Directory designed by ISDecisions. It works alongside Active Directory to protect access to Windows systems. With specific and customizable user login rules and real-time monitoring, UserLock reduces the risk of external attacks and internal security breaches while helping to address regulatory compliance.
UserLock is a user login security system for on-premises Windows Active Directory designed by ISDecisions. It works alongside Active Directory to protect access to Windows systems. With specific and customizable user login rules and real-time monitoring, UserLock reduces the risk of external attacks and internal security breaches while helping to address regulatory compliance.UserLock is one of the few solutions existing on the market that allows implementing multi-factor authentication for logging on to Windows computers with Active Directory domain membership.
UserLock can be used with hardware tokens and the compatibility with Token2 programmable hardware tokens has been officially confirmed by ISDecicions, and the enrollment guide is available on the UserLock website. Our hardware tokens can also be used to secure access to Microsoft Office 365 services by leveraging Azure Cloud MFA, however, there is currently no direct integration between Azure MFA and UserLock and each service would need a separate hardware token per each user, which is rather inconvenient.
In this article, we will show a workaround that allows using one hardware token for a user to access both UserLock-secured Active Directory and Office 365 services.
Prerequisites
The following will be needed:
- A Token2 programmable hardware token (any model would work)
- An NFC Device and a burner application for burning the seed. We currently have Windows and Android applications available (and iOS13+ for the most recent models, with part numbers ending with "-i", for example, C301-i )
- UserLock system installed
- Global tenant admin access to Azure AD (Microsoft Entra ID)
- Azure AD (Microsoft Entra ID) Premium (P1 or P2) licenses for each user being enrolled
A. UserLock provisioning
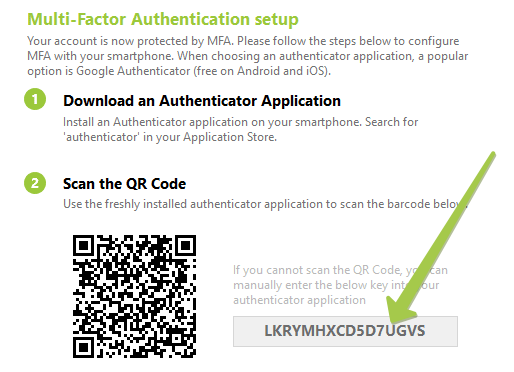
Please refer to the guide published by ISDecisions: Onboarding for End Users – with a Token2 programmable token.
On Step 2 of the guide, the system generates a base32 seed which has to be recorded for Azure MFA provisioning. Copy the seed shown on the provisioning page to a text file and have it ready for the next phase.
B. Azure MFA Provisioning
Prepare a CSV file in the following format using the base32 seed recorded in the previous step. The format will be as follows:
upn,serial number,secret key,time interval,manufacturer,model<[email protected]>,10000001 , <SEED>,30,Token2,C301
Replace the following values:
<[email protected]> replace with the UPN (email address) of the user being provisioned
<SEED> replace with the base32 seed recorded on the previous phase
Save the file with CSV extension. Important: make sure you use a plain text file editor, such as Notepad or Notepad++. Editing this file with Excel may break the format. Import the CSV file to Azure MFA as described in the guide.
After completing the activation with Azure AD (Microsoft Entra ID), the same hardware token can be used for both systems.
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
